Originally published December 14, 2020. Last updated January 11, 2021.
The wide-spread extent of the SolarWinds security hacks and the release of FireEye’s penetration tools is probably the most significant network security event since the WannaCry ransomware attack in 2017.
Summary
This attack has the potential to compromise your entire infrastructure. To gauge the extent of the threat – please realize that the US Cybersecurity and Infrastructure Security Agency (CISA) and the US Department of Homeland Security (DHS) issued their Emergency Directive on Dec 13, 2020 requiring that all US Federal Departments should turn off or disconnect their SolarWinds Orion systems by Noon Eastern on Dec 14, 2020.
January 6, 2021: The CISA directive has been updated explaining specific steps that should be followed. We’ve updated this article as a result—see below.
This is unprecedented and the investigation is ongoing. The actual depth and breadth of the attack continues to grow as investigators uncover more data. The latest reporting by the New York Times suggests that more than 250 organizations have been affected, including federal agencies and major businesses like Microsoft and Amazon.
What should you do if your organization is one of the 300,000 customers of SolarWinds and FireEye? Our security team has some recommendations on steps to take and how to handle the situation.
Assess the Situation
First, if your team runs SolarWinds Orion, was that version at risk?
- The vulnerable versions were released between March 2020 and June 2020 as documented in the SolarWinds advisory. Many organizations don’t update their applications very frequently, so have the network management tools team determine if a vulnerable version was ever used.
- CISA Update: January 6, 2021: CISA updated Emergency Directive 21-01 with explicit steps that must be followed. Note that you must scroll down to find the section titled Supplemental Guidance v3, dated January 6, 2021. Agencies that ran the affected versions of SolarWinds Orion must conduct forensic analysis to detect additional actions by the threat actors. Any further use of SolarWinds must comply with hardening requirements. Finally, report to CISA.
- CISA Update: December 30, 2020: All affected versions should be powered down or otherwise removed from Federal networks. The directive also clearly states that any system that previously ran an affected image must be treated as compromised. No system that ever ran an affected version should remain online. In addition, both unaffected and other versions must be upgraded to Orion Release 2020.2.1HF2.
- CISA Update: December 18, 2020: SolarWinds Orion version vulnerability list has been updated. In addition, for Clarity, the Versions of SolarWinds Orion were broken into three groups: 1) The ‘affected’ versions (containing the malicious backdoor), 2) The versions having been identified as not having the backdoor (‘unaffected’) and finally 3) Other versions. This clarifies the actions needed, but all other aspects of the ED 21-01 remain in place.
Then, if a vulnerable version of SolarWinds was used, you need to understand that many implementations involve read and write access to your infrastructure – meaning a compromise would have permitted the attacker to modify your infrastructure and systems.
- How is Orion used at your Company?
- Were any unauthorized firewall rules deployed from it?
- Were any unauthorized changes made to router, switch or other infrastructure devices?
- Have you lost any data?
A security information and event manager (SIEM) may help the security team identify potential data loss. At this point, it isn’t clear what data was of interest, so have them look for anything out of the ordinary.
The attack on FireEye didn’t impact their products (to our knowledge). Instead, their penetration testing tools were stolen and may be used by this or other bad actors in the future. FireEye has published a link to its list of countermeasures (a technical list of penetration tools and mitigation for each).
What Next?
How should you and your organization proceed from here? Our security team has created a list of next steps to help you navigate this threat:
- Monitor CISAs announcements for guidance at https://cisa.gov. There is already an emergency directive in an announcement of the compromise and a corresponding Emergency Directive 21-01. You should have your IT security team review and act on its recommendations. January 6, 2021: The revised Directive contains a table summarizing conditions under which SolarWinds Orion may be continued to be used:
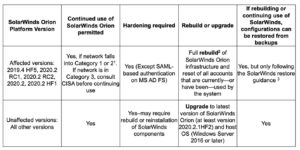
- The first step is to disconnect SolarWinds from the network or to turn it off. If your organization can do forensic analysis, follow the directive and do this first. If that capability doesn’t exist or cannot be done quickly, turn SolarWinds Orion off until CISA releases a new recommendation. When the industry determines that SolarWinds is safe, plan to build a new SolarWinds implementation. January 6, 2021: This is what CISA is now requiring.
- Then your IT security team should assess whether any of the systems monitored and managed by SolarWinds have been compromised or had unauthorized changes, especially firewall rule changes or unauthorized software updates or installations. A variety of tools can help with this process – please contact us if you need guidance. The security team should also evaluate system access logs to determine if any lateral movement of a potential attacker is detected.
- FireEye’s penetration tools were stolen, and you should consider your organization vulnerable until your IT security team proves otherwise. FireEye’s security recommendations should be followed, as published in a detailed threat research document (useful for your IT security team): Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims with SUNBURST Backdoor.
- January 6, 2021: Also review CISA Alert (AA20-352A) that describes other threat vectors. Any systems which SolarWinds Orion was able to manage (i.e., had read/write access credentials or read access to sensitive data like login information) should be rebuilt.
This security compromise is very disruptive to businesses who are busy trying to remain ahead of other threats. NetCraftsmen is tracking the events and is prepared to assist with an analysis or structuring of an alternative network management system.
Updates will be posted on this site as we evaluate CISA and appropriate vendor advisories.
For more information or if NetCraftsmen can help, please contact our Chief Technology Officer, John Cavanaugh directly at [email protected].
