Organizations need an Information Security strategy, regardless of their industry or annual revenue. But where do you start? And once you start, how do you ensure that the security strategy is being implemented correctly and maintained over time? “Architecting an Information Security Program for the Enterprise” discusses a practical approach, start to finish, on how to plan, build, implement and maintain an information security program for the modern-day enterprise.
Knowledge is power. It is self-evident that computing technology has permeated every aspect of our lives. We use computers at work, and we play on them at home, we watch movies on tablets, we check email from our watches, make credit card purchases with our mobile phones, and adjust our Internet of Things (IoT) home appliances over the Internet.
These technological advances allow us to be more productive and more entertained but also create a large set of security risks. If we can gain knowledge about information security concepts and how to apply them, we will have the ability (or the power) to evolve alongside the everchanging technology landscape.
What is information security? According to US law 44 USC, Sec. 3542, information security is defined as [the process of] “protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction.”
In short, information security means protecting our IT assets. The manner in which we protect our assets and the opposing forces we protect our assets from will vary greatly. Natural disasters, power failures, disgruntled employees, and of course, malicious threat actors against our network are all undesirable states or events.
In our place in history, we find that our information assets, such as data, are equal to if not more valuable than our physical assets. We must also protect our people, both in a physical sense and in a productivity sense. People are our most valuable asset, and without them, the wheels of commerce come to a grinding halt.
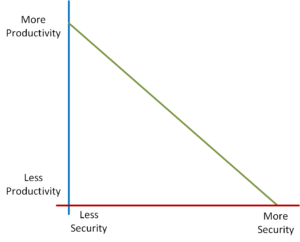
There is typically an inverse relationship between productivity and security – as one increases, the other decreases. For example, we can place extremely high-security levels around every asset we control, but at what cost to budget and productivity? If we place razor wire fencing, double-door biometrics, finger-print controls, and ten layers of firewalls to prevent unauthorized access to a server containing publicly accessible information, is this a useful trade-off for employee productivity? Is this a compelling return on investment from the information security budget? We must negotiate an effective balance.
CIA Triad
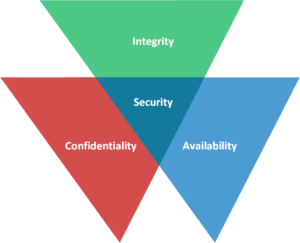
By definition, information security means protecting our assets, and more specifically, our information assets. In practice, information security means applying the principles of confidentiality, integrity, and availability in balanced measures such that there is overlapping coverage of each. In a Venn diagram, the region where these principles overlap Is information security.
Confidentiality – We must ask, what happens if the wrong person gains access to the data? To address this element, we must put controls or mechanisms in place that ensure only authorized people can access the data. An example would be multi-factor authentication. This uses more than one of the following categories to authenticate yourself: something you have (token), something you know (password), something you are (biometrics). Another example would be data encryption. For further reading on confidentiality and its role in information security, see our blog CIA Triad: Part 1 – Confidentiality.
Integrity – We must ask, what happens if someone unauthorized changes the data? To address this element, we put mechanisms or controls in place that ensure data remains unchanged from its original state– at rest, in transit, or in use. An example would be using a hashing algorithm to create a hash (or fingerprint) of the file and then later running that algorithm again to create another hash. If the hashes match, then we can ensure the file has not been altered or changed. For further reading on confidentiality and its role in information security, see our blog CIA Triad: Part 2 – Integrity.
Availability – We must ask, what happens if someone unauthorized deletes the data or makes it unavailable? To address this element, we put mechanisms or controls in place to ensure that resources are available for authorized people when needed. A few examples would be fault-tolerant disk systems (such as arrays) or redundant power supplies for those systems. For further reading on confidentiality and its role in information security, see our blog CIA Triad: Part 3 – Availability.
The CIA triad is the foundation on which we build our information security program, and there are two leading schools of thought on how to accomplish that – using a compliance-based approach or a risk-based approach.
Compliance-based information security programs focus on satisfying the legal and/or regulatory requirements of the industry in which the organization is operating. A compliance-based information security approach is usually more palatable for smaller organizations, for those with fewer security resources or a less mature security program. Compliance-based information security programs tend towards a “checking the box” mentality in order to satisfy auditors and various regulatory requirements to which they are subject. While meeting compliance requirements and passing audits are most certainly paramount, it is essential to remember that these requirements exist to set minimum standards for protecting the customers that we serve.
Compliance requirements are not meant to take the place of intentionally developing a sound foundation for information security based on the organization’s specific needs. If we allow our information security program to develop organically, we wind up tacking things on in a reactive way as we encounter specific issues, audit findings, and other such drivers. The result is we will likely end up with an unbalanced security program.
Risk-based security programs represent the more planned and intentional methodology for constructing a security program because it is based on the actual risks that pertain to the organization, not generic requirements. The risk-based approach usually results in a stronger information security program and accomplishes compliance as a by-product. However, a risk-based approach is also more resource-intensive and may not apply well to all organizations, particularly those that are very small in size or with tight resource constraints. If given the option, a risk-based approach is recommended and will be discussed in greater detail. A risk-based approach does not mean we disregard compliance; it simply means that compliance becomes one factor in our decisions making rather than the driving force.
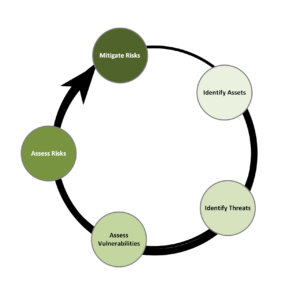
The risk-based approach embodies an iterative process of Identifying information assets, identifying the threats to those information assets, assessing vulnerabilities, assessing the risks of those vulnerabilities, and finally mitigating the risks. This process of asset identification, threat identification, vulnerability assessment, risk assessment, and remediation, as depicted in the figure below, is continuously repeated as the organization changes and as new threats emerge.
Vulnerabilities are a weakness that lacks protective countermeasure. A threat is the danger of something or someone taking advantage of a vulnerability. Risk is how likely it is that a threat will exploit a vulnerability. A control is something we install or perform in the environment to mitigate risk.
In the next blog in this series, we will discuss using a risk-based approach to plan out our information security strategy in greater detail.