I thought I would share a quick tip: When you have Cisco Access Control Server (ACS) integrated with Microsoft Active Directory (AD), you can use an SSH session to a Cisco device to update your AD password.
ACS Configuration
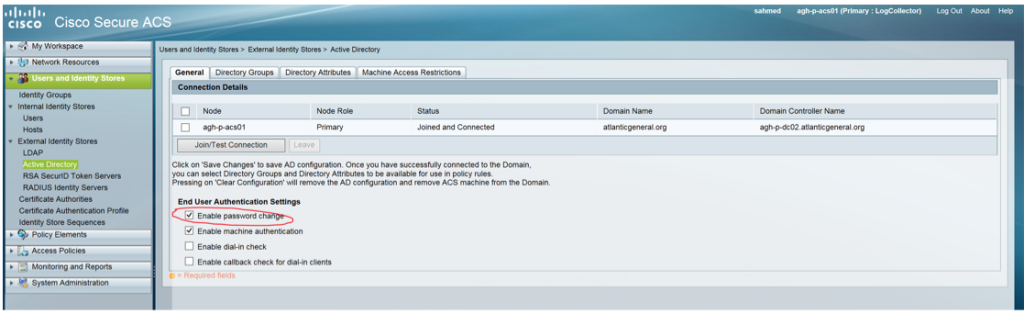
You need to set the End User Authentication Settings for AD in ACS to Enable Password Change.
Simple Process to Use
When you are first prompted for your AD password by a Cisco device, press the Return key. You will see a prompt for your old password, and then two prompts for your new password.
If you enter a new password twice, the session should look something like this:
~ cwr$ ssh -l creece 10.255.5.1 password: Enter old password: Enter new password: Enter new password confirmation: sw-01-dist#
This process also seems to work with Telnet, if your device allows Telnet access:
~ cwr$ telnet 10.255.5.1 Trying 10.255.5.1... Connected to sw-01-dist Escape character is '^]'. username: Kerberos: No default realm defined for Kerberos! creece password: Enter old password: Enter new password: Enter new password confirmation: sw-01-dist#
Note: I typically recommend that you do not allow Telnet access.
Compliant Passwords Required
Note that ACS is really tied in with the AD rules – if you try a non-compliant password (such as too short or too recent previous password or other AD password issue), the password change attempt will fail. If you look on ACS, you will see why:
24411 Change password against Active Directory failed since user has a non-compliant password
Summary
I sometimes find this process helpful so I can update my AD password without logging into an AD domain device.