This blog is a follow-up to two prior blogs about Elisity. I suggest reading them first if you have not already done so.
This blog covers the recently announced Elisity Version 15.0 release, which brings us some nifty new features and improvements.
As with some of my other vendor-specific blogs lately, I intend to whet your interest, give you a summary, and entice you to check things out in more detail. Speaking of which, for the full story, see Elisity’s blog about 15.0. After you read this blog, of course!
The focus of the changes is enhancing the power of the user interface, making it easier to build identity/attribute-based policies, and adding new capabilities to all that.
Summary of Prior Blogs
Elisity is a Zero Trust campus security and micro-segmentation product, targeting not only most organizations but especially entities like hospitals and manufacturing, with a strong need to isolate IOT devices from users, etc. Part of Elisity’s approach is to emphasize “Rapid Time to Value” in the product. I’m told the solution can be deployed in a couple of hours, with policy created and applied soon after that.
I used the word “campus” above to emphasize that Elisity is about Zero Trust in the sense of users and devices and what traffic is allowed between them. It is not currently about controlling and securing external access per se to applications the way a firewall might. Having said that, Elisity can define apps and control micro-segmentation to/from apps in the campus or data center.
The key to how it works is:
- Native discovery and integration with other tools permit Elisity to learn about users, devices, and attributes (user identity, device vendor, device model type, software version, IP address, etc.)
- Policy groups are operator-defined using match criteria based on any user/device/custom app attribute learned or defined previously. Example: “Secure Radiologists Policy Group” = Radiologists using Dell Inspiron 5530s that are known in the CMDB.
- Policies you create then control who or what can talk to other entities. Think of them as access-lists but based on user or device attributes rather than IP addresses. They control traffic between policy groups.
- For example, a Policy might then allow Secure Radiologists to access Radiology devices and databases (and probably printers and some other things as well).
So, What’s New?
Here’s Elisity’s list of “key improvements” in 15.0 (my wording). They center around policy groups:
- A Clear and Concise User Interface:Simplification of the policy group creation process to focus on what matters.
- Enhanced Guardrails:“Guardrails” guide you through each step of the process to avoid mistakes and streamline your workflow.
- Support for Policy Group Descriptions:You can now add descriptions to your policy groups.
- Improved Filtering Options:Broadened filtering options for more control and flexibility when creating your policy groups.
- Simplified Menus:Fewer menus to click through.
- Efficient Editing and Deletion:Modifying or removing a policy group and its match criteria is now more efficient.
What’s It Look Like?
Let’s take a look at some screen captures covering some of those enhancements.
The screen for editing a policy group now shows matched assets, which provides a sanity check on the criteria you’ve created for members of the policy group. Note also the button for adding new criteria.
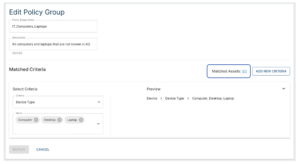 (Diagram courtesy of Elisity, used with permission)
(Diagram courtesy of Elisity, used with permission)
The Policy Matrix has been enhanced, as can be seen below.
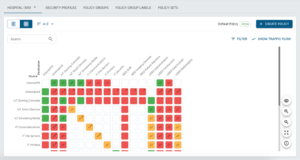 (Diagram courtesy of Elisity, used with permission)
(Diagram courtesy of Elisity, used with permission)
The color or shading indicates permit versus deny all, or a mixed rule policy.
The arrows indicate one-way versus two-way policies. Previously by default, Elisity automatically created rules allowing return traffic. You can now explicitly create one-way-only rules, that allow traffic in a single direction. “Unidirectional Policy Support”.
Improved search, sorting, and filtering features, as well as custom views. For example:
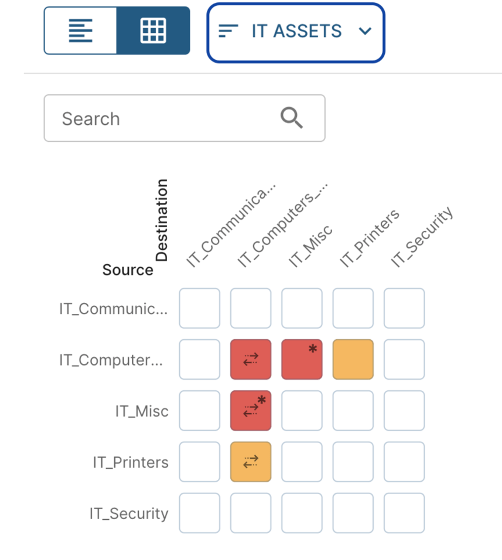 (Diagram courtesy of Elisity, used with permission)
(Diagram courtesy of Elisity, used with permission)
An example use might be a per-site custom view for each hospital, clinic, or corporate site/HQ.
More Goodies!
There’s now a Simulation Mode, providing a view of how your policies would affect traffic flows and assets. That gives you a chance to revise policies or changes before deploying them.
Elisity cites the following ways in which Simulation Mode can be helpful:
- Comprehensive Policy Insights:Visualize how your policies would affect traffic behavior and asset accessibility.
- Policy Testing and Refinement:Experiment with various policy setups and observe their effects on your network.
- Enhanced Security Posture:Proactively identify and rectify potential security vulnerabilities. By visualizing the effects of your policies, you can spot unintended consequences, blocked connections, or unauthorized access attempts, strengthening your overall network security.
- Operational Risk Mitigation:Identify potential disruptions or performance issues in a simulated environment before they affect your live network.
- Seamless Integration:Unified interface to manage both enforced and simulated policies.
There are three Trust attributes in Elisity: Check CMDB, Check AD, Manually Verified. The point to these is that Elisity can check the CMDB (e.g. ServiceNow) or Active Directory before adding a device to a policy group. Or it can confirm if the device has been manually verified.
I think of this as “Who You Gonna Trust?” (my wording).
Here’s how Manually Verified works in practice, as a match criterion in a Policy Group. Only manually verified and trusted devices will match the Policy Group. A field in the Device Info screen is where you confirm that the device passed manual verification. See the following screen capture:
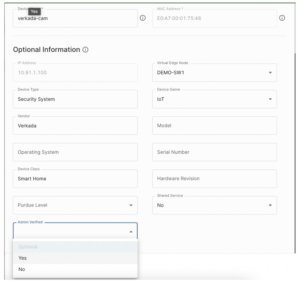 (Diagram courtesy of Elisity, used with permission)
(Diagram courtesy of Elisity, used with permission)
Conclusions
Elisity continues to focus on user and device identification and policy controls, while expanding and simplifying administration and management capabilities.
Strong rumor says Arista and Juniper support is in the works.
In short, neat stuff!
Links
Useful links:
- Elisity
- Elisity Resources Page (Videos, Solution Briefs, White Papers)
- Elisity Knowledge Base (documentation, found under Support)
- Elisity’s YouTube Channel
- Elisity’s Blog Page
- Elisity’s Connectors and Integrations
- Switch compatibility list
- Gartner: https://www.gartner.com/reviews/market/network-access-control/vendor/elisity/product/elisity-cognitive-trust
Content specifically relevant to this blog:
Let’s start a conversation! Contact us to see how NetCraftsmen experts can help with your complex challenges.



