Forward Networks presented at Cloud Field Day (#CFD) 16 in January of this year. They’ve been on my mental “interesting company to watch” list since I was at their launch in 2017. That’s in no small part because they’re a strong player in the network/security Digital Twin product space. (See also my recent blog on that topic.)
This blog updates what I’ve previously posted regarding Forward Networks. And yes, there’s been some latency in getting this published.
What Does It Do/How Does It Do It?
I understand that Forward Networks’ development process starts with lab testing: they intelligently “bombard” configured networking devices with traffic, currently running 120,000 tests per device.
The goal is to understand how each device configuration element affects traffic. It then captures and stores that information internally. This has the benefit of actual verification, as opposed to what an expert believes the device will do.
From prior presentations: this is based on forwarding equivalence classes, i.e., a representative flow from each ACL range, prefix in routing, etc. – they do not have to send a packet with each TCP/UDP port, etc., to get an accurate read on device behavior.
The device’s behavioral data is then “baked” into the product to model the forwarding of traffic flows. Presumably accurately, even down to vendor quirks.
When deployed in your network, Forward Networks discovers devices, collects network device configurations, connection information, ‘show’ command output, etc., using read-only access to network equipment that you provide. This data is stored with a retention policy you can specify, and with different levels of user access to the data.
Alternative topology and inventory collection means can be used (for example, on secure financial networks).
Forward Networks can then detect changes and predict your production network’s behavior. It can answer questions, such as will traffic from A to B on port C be allowed, and where will it be blocked if blocked?
The initial marketing was mainly focused on access list/forwarding behaviors: troubleshooting or predicting which flows would or would not be blocked and where. As well as specifying intent and identifying potential gaps in security policies. Forward Networks is now building on that, focusing on also serving as a network assurance tool.
The following graphic indicates some of the ways that can be used to manage Security:
There are two obvious ways to expand the product’s capability: support more devices/vendors, and more protocol behavioral testing. Apparently, Forward Networks has done both.
There’s also the challenge of keeping up with the customer base. What’s new? Cloud is obvious there, as it does routing, security/firewalling, etc. And so, collecting cloud state data and modeling cloud behavior is now something Forward Networks does.
Diagramming is also a crucial part of what Forward Networks does. That can be helpful for understanding the current network connectivity and visualizing the paths and devices used to forward a specific traffic flow.
Forward Networks says their software is fully API accessible, and they have Slack and ServiceNow integrations.
But Cloud?
So Forward Networks will discover and diagram your cloud footprints, currently with the three main CSPs: Amazon, Azure, and Google. As some other tool vendors (e.g., Kentik) have realized, visualizing what you have at the moment in the cloud is highly valuable, significantly when DevOps teams may be changing things on the fly.
Here is what a Forward Networks CSP diagram looks like:
Apparently, Linux-based networking is coming soon, and Kubernetes(K8S)/container visualization is on the roadmap.
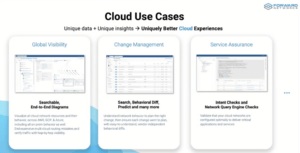
Here is a graphic showing some cloud use cases:
An Analogy
Forward Networks uses Google Maps as an analogy. Their process determines road connectivity and distances for the basic display. And they can display various search findings and attributes on the map E.g., where toll booths are, one-way streets, etc.
Forward Networks discovery does the networking counterpart of that. Connectivity (road map) and attributes (of links and devices). And then can make inferences based on that.
Use Cases
The #CFD presentation also included some use cases. I’ll mainly leave that for the video if you want to see use cases.
One use case is Blast Radius: what is affected if a device fails, an access list gets removed, etc. Analysis of “What Ifs” in general.
Another is Goldman Sachs, which is both a customer and big investor in Forward Networks. See the link below for a 2022 ONUG video. Or register on the Forward Networks website to download the case study.
Another use could be for new hires, using the automatically generated diagrams to familiarize them with the network.
Some of the NIST CVE database has been incorporated into the product, allowing checking for devices with security problems. CIS, HIPAA, and STIG reports are built-in via a library; a user community to add such tools is (was) reportedly in the works.
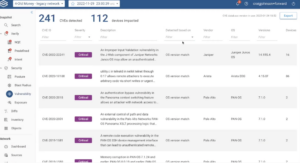
The following graphic illustrates reporting based on this information:
The #CFD presentation did mention innovation on top of the digital twin as well, in a Hackathon. Examples of code using Forward Networks included using it to “find all printers” and a Change Management workflow, including validation by Forward Networks. See also https://www.forwardnetworks.com/support/ and https://www.forwardnetworks.com/global-entertainment-company-saves-hundreds-of-it-hours-every-year-with-forward-networks/.
Company Status
My impression, corroborated by some others, is that Forward Networks has had very solid customer growth since its launch. Some very large financial and other companies use it to provide network security assurance and solve application flow problems in large complex networks. That solves problems that would be very costly and time-consuming to do in any other way.
The product can be deployed on-prem or in the cloud (AWS SaaS) with an on-prem collector application (for security reasons).
Licensing is based on the number of devices, not the number of users. The SaaS cloud offering uses a credit-based system (instances and time).
The product also does what I’ll call tenants, so an MSP can use it to model customer networks.
Limitations
The company is focused on the assurance role. It does not push changes to network devices. That’s where you might use Ansible or Terraform to make actual changes after modeling them in Forward Networks. The video indicated that future state modeling is on the roadmap.
You can currently use Forward Networks for merger scenarios: discover each of the two networks, then run a combined model where you add connectivity between the two. (Details omitted.) So, “future state modeling” seems like it might be something more complicated than introducing some connections or a pseudo-device or two.
Links
Goldman-Sachs video: https://www.youtube.com/watch?v=qTOLROZqih0
Goldman-Sachs case study: https://www.forwardnetworks.com/goldman-sachs-case-study/
Gamified demo: https://www.forwardnetworks.com/forward-quest/
Use Cases: https://www.forwardnetworks.com/resource-library/?_type=use-case
My blog discussing different types of Digital Twins: https://netcraftsmen.com/digital-twins/
Conclusion
If you need a way to validate your company’s security posture or quickly resolve complex problems with application flows being blocked by ACLs, etc., you might want to look at Forward Networks.
Let’s start a conversation! Contact us to see how NetCraftsmen experts can help with your complex challenges.