Zero Trust is a data-centric approach to security. This involves identifying the data assets that need protection and creating a data classification policy. With this information an Enterprise Information Security Policy (EISP) can be developed to drive an “All of Enterprise” approach to security.
So, what exactly is a “data-centric” approach?
Data-Centric Security
As a data-centric methodology, Zero Trust is essentially a risk-based approach to security.
So, what does this mean and how do you start?
Every firm needs an Enterprise Information Security Policy (EISP). This details an enterprise’s philosophy on security and the direction and tone of a firm’s security efforts. Central to this effort is defining what data needs to be protected, where it resides and how it is used.
Unfortunately, this is not as straight forward as it might appear. For example, when someone thinks about a hospital – electronic medical records (EMR) come to mind, but hospitals are also large employers with personally identifiable information (PII) on employees and contractors. In addition, they often operate as retail businesses with corresponding payment card industry (PCI) compliance requirements.
More topical – since the Colonial Pipeline attack – is that many organizations also operate real-time systems (often called IoT or OT systems) that can impact the physical world. Some IT teams are not even involved with the management of these systems. In some enterprises this may involve simple CCTV systems and/or door locks, but there are others – such as utilities – that are controlling water, sewer, gas, and electricity delivery systems.
In the case of our example hospital, it will also have hundreds to thousands of IP-based instruments ranging from patient monitors, infusion pumps all the way up to, and including, complex radiological devices and even robotic surgical systems.
This all results in vital data and control systems that cross multiple regulatory boundaries all requiring protection.
Understanding the data and having your business risk team evaluate the costs of being denied access to it are key to producing a risk based EISP.
Systems Inventory
Putting the new policy-based plan into action requires a systems inventory of all your assets and operational practices. The NIST Cybersecurity Model outlines five operational functions that are applied to five asset classes. NetCraftsmen has adopted the Cyber Defense Matrix which literally maps the NIST 800-53 operational functions against their asset classes as shown in Figure 1 below:
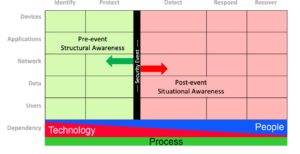 Figure 1: Cyber Defense Matrix (CDM)
Figure 1: Cyber Defense Matrix (CDM)
The operational functions are Identify, Protect, Detect, Respond, and Recover. The Asset Classes are Devices, Applications, Networks, Data, and Users.
Two axioms exist in security:
- You can’t protect what you can’t see
- To alert on abnormal behavior – you must have a baseline of normal behavior
On the operations side these represent pre-event structural awareness. This is where an organization must have a proper census of the user base and what they have permission to do with regards to devices, networks, applications, and data access. The relationships between asset classes and their operational use will establish operational awareness.
It’s also a good idea to map the product and solutions your enterprise uses onto the CDM to uncover areas of overlap or to illustrate gaps.
New Recommended Management Processes
In addition to the risk based EISP and a cascading set of policy and communications, several items need to be done:
Crisis management plans need to be in place, and they require:
- Emergency contact numbers for all key personnel
- Contact information for external providers like ISPs and managed services
- Hardcopies of all runbooks – tiered to support individual business units and functions
Of course, all of this must cascade from the top down and each set of business processes and all IT systems (on-premises, in the cloud, or through software-as-a-service) need to be documented.
Risk-Based Technology and Operational Changes
From a management standpoint there is a risk-based methodology called the “CIA Triad”: Confidentiality, Integrity and Availability (CIA). Confidentiality means that only authorized users and processes should be able to access or modify data. Integrity describes that data should be maintained in a correct state and nobody should be able to improperly modify it, either accidentally or maliciously. Finally, Availability describes that an authorized user should be able to access data wherever and whenever they need it.
From a technological standpoint the methodology is implemented as follows:
- Confidentiality – Encryption in transit and encryption at rest, role-based access, and identity management
- Integrity – Trust that the data has not been maliciously modified, including reliable backups for all data – preferably backups that were offline and not susceptible to a network hack (for example immutable storage) and file permissions
- Availability – Network, storage and system design that assume that failures will and do occur; proper upgrades and patching
Finally, proper instrumentation needs to be developed and deployed:
- Large outflows of data should be detected, and alerts should be established (data loss prevention)
- Behavioral analytics should be deployed – to react to unusual or non-standard changes in the environment
Ongoing Call to Action
EISPs and the downstream technological policies need to be living systems and kept up to date as the business evolves and changes. As a result, a governance process needs to be established to tie the senior management team with the technology teams tasked with protecting and managing the firm’s data assets.
As always NetCraftsmen consultants are here to assist and guide your journey to a more secure future.
