Did my Networking Field Day (#NFD13) blog about Forward Networks (@FwdNetworks) catch your eye? Do you need to verify that changes won’t break your network? Or that there are no loopholes in your security?
Forward Networks defined a somewhat new network and security tool category with its announcement at #NFD13. Specifically, “Network Assurance” — making sure your network and changes will meet your specifications of correct behavior. See the blog I wrote for more about Forward Networks.
I say “somewhat new” since the Netsys product that Cisco acquired and then dropped did some of the same things: network modeling, path calculation, flow validation. Forward does it via a newer approach, massive computation and testing, based on Stanford Ph.D. research.
Well, Forward has some established competition…
Introducing Veriflow
The folks at Veriflow demonstrated their product for me recently. Veriflow is a San Jose-based company, with a product based on researchers with UC Berkeley and University of Illinois backgrounds (for those who like comparing academic heritages).
There are some real similarities in function between the products from each company. Veriflow touts their product as “continuous verification” of a network. The main idea is to make sure your network’s behavior matches your intentions. Or “intent-based networking.”
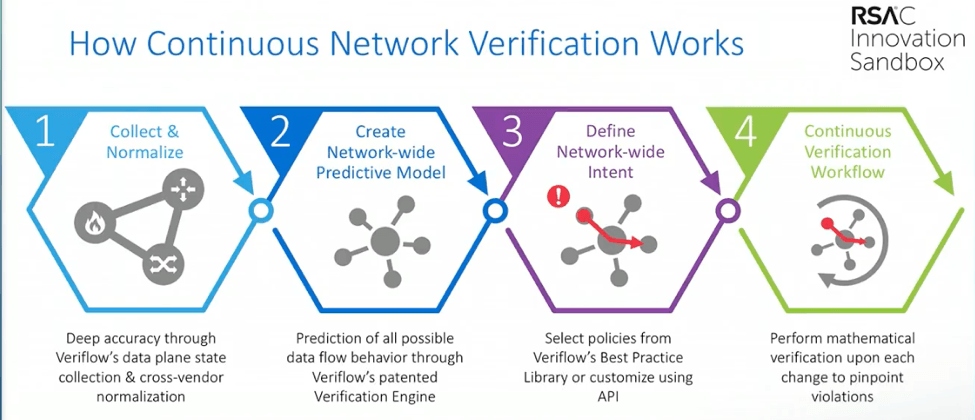
Veriflow focuses on four main objectives:
- Network segmentation and vulnerability detection
- Continuous compliance and dynamic mapping
- Network availability and resilience
- Rapid incident response
All this is based on pulling in information (described as show command output and configuration information) from devices, and building a topology model. From personal experience, trying to map a network, fitting firewalls into that can take a good bit of work due to lack of CDP or LLDP.
The network model is then used together with formal verification modeling, with optimizations based on the network context, to determine the path taken by any flow. If the flow is blocked, that fact along with the reason why is detected and retained.
Rapid Incident Response is inherent in this approach. If A on source port B can’t talk to C using destination port D, presto, you already have computed the path and the reason. I gather that occurs not for an individual flow but for the equivalence class of such flows (somewhat analogous to MPLS FECs).
Veriflow’s marketing is perhaps leaning a little harder on the security angle to this than what I picked up from Forward Networks — which might just be my sensitivity at the time of demo. Veriflow is claiming to detect violation of compliance rules and the ability to enforce network segmentation. Cool stuff!
Here’s a sample including detection of segmentation verification:
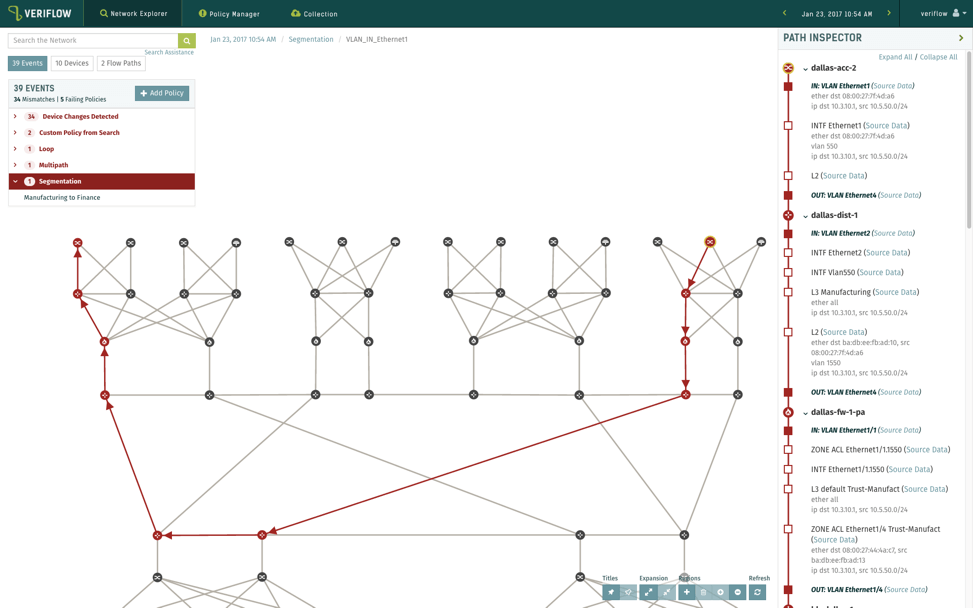
The Hard Part
The potential issues appear to be the same as those I listed in the Forward Networks blog. Specifically:
- How comprehensive is the configuration to model mapping?
- How easily can one build the policy database?
The first of these bulleted challenges includes functionality in the model. It sounds like Veriflow models VRFs for segmentation, possibly. Does Forward Networks? I have no idea. Does either model policy-based routing? What about the numerous subtleties of BGP?
For Forward Networks, it sounds like modeling would entail configuring features or combinations of features and observing what they did to packet flows on a single device basis — in effect, sending flows from each equivalence class to a configured device.
For Veriflow, I have no guess at what they’re doing to build the mapping of CLI to packet forwarding behavior.
The reason I bring this up is that this was clearly one of the challenges for the old Netsys product, as new and more complex functionality kept being added to the routers. (What, Cisco, lots of new features and some complexity?)
Concerning the second bullet above, policy database, this strikes me as sort of the access list from the Nether Regions problem. Can you (or do you even want to) specify every flow you want allowed and disallowed in a reasonable amount of time?
I’m coming up with “sort of.” For compliance and segmentation, one probably wants to know that address block set A can’t talk to those in set B, period. That might be a fairly concise rule to state. “No outside IP can talk to these subnets” — OK, doable. But then it gets messy.
Do you white-list all the current permitted flows? But then you accept any holes in the present security coverage.
The best alternative might be to learn all application flows that actually occur, and allow them. That makes the large assumption you have no malware or security breaching flows. It also assumes you have a massive flow tool like Cisco Tetration or AppDynamics, thoroughly deployed.
Of course, when designing firewall rules, we already have that problem. We usually prioritize and tackle it incrementally. And one can do that with these tools as well. I also see this problem arising with micro-segmentation, of either the ACI or NSX variety. What may help is to back up and start with a clear security policy, instantiated via meaningful objects rather than ad hoc per-host or per-host group rules. But that’s a topic for another blog.
More About Veriflow
- If you check out Veriflow’s website, you’ll find a number of awards and some big-name references.
- You might find Googling “Veriflow equivalence class”
- There are several YouTube videos by Veriflow.
- Veriflow Named a 2017 Cool Vendor in Enterprise Networking by Gartner
- How Next Gen Analytics and Verification Helps Realize Resilient, Secure Networks — Blog by Brighten for ONUG
- Cool Network Vendors 2017 — Andrew Lerner blog post
Ask us about our network and other assessment services. We sample your network to identify design and performance issues, and failure to follow configuration best practices. Learn more.
Comments
Comments are welcome, both in agreement or constructive disagreement about the above. I enjoy hearing from readers and carrying on deeper discussion via comments. Thanks in advance!


