BlueAlly/NetCraftsmen’s Joel King has been experimenting with tools from pangea.cloud. This blog tells you about that. Thanks to Joel for his Pangea testing efforts, his review of this blog, and for helping me with some of the questions and knowledge gaps I had.
Pangea provides cloud-based security services to developers. “Security Platform as a Service (SPaaS)”.
Joel’s insight was that this might be useful for some settings where you’re trying to automate security checks as part of workflows, e.g., onboarding new staff, students, etc.
See below for some of the other security micro-services Pangea provides that you can call from your code.
Joel recently presented an RTP Meetup session about Pangea and some of the experiments he conducted with it and has made his sample code available. See the Links section below.
What is Pangea?
The original use of the word “Pangea” is as the name of the single mega-continent that existed a very long time ago.
As for the modern company Pangea, here’s what they say about themselves:
“Pangea offers foundational security services such as Authentication, Authorization, Audit Logging, Secrets Management,
Entitlement and Licensing. Other security functions include PII Redaction, Embargo, as well as File, IP, URL and Domain intelligence.
Take the smart path and integrate Pangea into your application. You’ll accelerate compliance, get into production faster, and deliver a more secure customer experience.
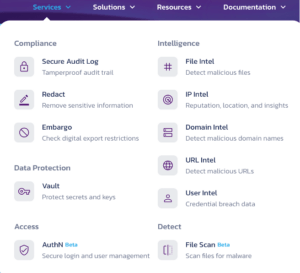
The following graphic on their website covers the services (micro-services) Pangea provides:
Some Specifics
Yes, that all sounds good, but what does Pangea actually do?
Pangea provides API-based access to cloud-based Security microservices. This allows you to easily and affordably add forms of certain security functionality as you automate selected Operational workflows.
Here are some of the microservice descriptions:
- Embargo: check where a web or other request is coming from to see if the location is subject to embargo, sanction, etc.
- File Intel: Check a file’s reputation, see if it might be malicious.
- URL Intel: Similar, but for URLs.
- Domain Intel: check a domain to see if it might be associated with bad actors.
- User Intel: look up user PII or credentials for compromise.
- Redact Service: ID and remove sensitive PII, financial, etc. data, with custom rules.
How do you access those services? Pangea has SDKs that can be invoked from node.js, Python, Golan, Java, Django.
Or Ansible, per the following …
Joel wrote an Ansible Content Collection that includes a Python module that can be called from Ansible to invoke the Pangea SDK. That enables using Pangea Intel Services (DNS Domain, URL, and User) as part of an Ansible workflow (playbook). This is available via the links below.
Joel ran Ansible directly from the CLI for demo purposes. You can also execute the same playbooks by using the Ansible Automation Platform as part of a production environment.
Practical Example
You’re onboarding a new hire or a new student and want to have an automated workflow.
That’s why Joel King was looking at Pangea:
The BlueAlly Consulting group has an active project to develop an automated workflow to manage the user database in Cisco Unified Communications Manager (CallManager) deployments. The BlueAlly Consulting group is engaged with a public university best known for its dental school, medical school, and college of engineering. The project is based on developing an Ansible Content Collection for the client’s Ansible Automation Platform to enable the workflow. Creating an Ansible Content Collection for Pangea User Intel, enables additional value to the client with a minimal development effort and cost.
Sample Ansible Playbook
As an example, here’s the Ansible code to check whether User Info is “breached” or known on the web.
(See the various links for more sample code. Also note that Pangea has a lot of documentation and collateral to get you started using their services.)
#!/usr/bin/env ansible-playbook
—
#
# Copyright (c) 2023 BlueAlly NetCraftsmen, LLC
# All rights reserved.
#
# author: Joel W. King, @joelwking
#
# description: Breached user check, verify if the username,
3 email or phone number has
# been exposed in a security breach.
#
# usage:
#
# ansible-playbook pb.breach_user_check.yml -e
# ’[email protected]’ -e ‘phone_number=9197079300’
# -e ‘username=bob’
#
# use `–skip-tags sendmail` to avoid sending an email.
#
– name: Breached User Check
connection: local
hosts: localhost
gather_facts: false
vars:
# Subject of the investigation
email: “[email protected]”
phone_number: 919-707-9300
username: whitehead
# Email (results) receipient
receipient: [email protected]
pangea_anchor: &pangea_opts
domain: “{{ lookup(‘ansible.builtin.env’, ‘PANGEA_DOMAIN’) }}”
token: “{{ lookup(‘ansible.builtin.env’, ‘PANGEA_TOKEN’) }}”
tasks:
– name: User Intel email
netcraftsmen.pangea.intel:
<<: *pangea_opts
action: user
parameters:
email: ‘{{ email }}’
raw: true
register: pangea_email
tags: [’email’]
– name: User Intel username
netcraftsmen.pangea.intel:
<<: *pangea_opts
action: user
parameters:
username: ‘{{ username }}’
raw: true
register: pangea_username
tags: [‘username’]
– name: User Intel phone number
netcraftsmen.pangea.intel:
<<: *pangea_opts
action: user
parameters:
phone_number: ‘{{ phone_number }}’
raw: true
register: pangea_phone
tags: [‘phone’]
– name: View output sample results
ansible.builtin.debug:
msg:
– ‘Phone: {{ phone_number }} {{ pangea_phone.data.summary }}’
– ‘Username: {{ username }} {{ pangea_username.data.summary }}’
– ‘Email: {{ email }} {{ pangea_email.data.summary }}’
– name: Write files containing the returned data for additional analysis
ansible.builtin.copy:
content: ‘{{ item.data | to_yaml }}’
dest: ‘{{ playbook_dir }}/files/{{ item.fname }}.yml’
loop:
– ‘{ “data”: {{ pangea_phone }}, “fname”: “phone”}’
– ‘{ “data”: {{ pangea_username }}, “fname”: “username”}’
– ‘{ “data”: {{ pangea_email }}, “fname”: “email”}’
– name: Send email
ansible.builtin.include_tasks:
file: ‘{{ playbook_dir }}/task.email.yml’
vars:
to_email: ‘{{ receipient }}’
reply_to_email: [email protected]
subject_email: Automated User Breach Intelligence
body_email: ‘Investigation results: email address ({{ email }}), username ({{ username }}), phone number ({{ phone_number }}) were exposed in a security breach.’
attachments_email:
– ‘{{ playbook_dir }}/files/email.yml’
– ‘{{ playbook_dir }}/files/phone.yml’
– ‘{{ playbook_dir }}/files/username.yml’
tags: [‘sendmail’]
Other Things You Should Know
Pangea has a free trial offering based on providing some credits to use their functions.
Joel King signed up and found that the cost of a single function call is very small. For example, 1,000 API calls (requests per month) for User Intel is $3.00. Domain Intel is $0.006 per request, or $6.00 per 1,000 API calls. Given those prices, the cost to incorporate the Pangea tools into a network operations use case would be trivial.
Note that Pangea is targeted at front-end app developers that may make several API calls for each user or subscriber. In our use case, the cost would not really be a factor.
For more about Pangea’s pricing, see the link below.
Links
Pangea: https://pangea.cloud
Pangea’s pricing: https://pangea.cloud/pricing/
Pangea’s Secure by Design (Developer Education page): https://pangea.cloud/securebydesign/
Meetup recording: https://www.youtube.com/watch?v=fgt_mlnbxH4
Ansible Collection to exercise the Pangea function to see if email address, username, phone number, IP address were exposed in a security breach: https://galaxy.ansible.com/ui/repo/published/netcraftsmen/pangea/
Ansible collection to interface with Pangea Cloud: https://github.com/netcraftsmen/pangea
Sample code that parses Cisco config files for PII, and invokes Pangea to see if the information has been breached: https://gitlab.com/joelwking/pangea_cfg_intel
Sample Ansible playbook for checking User Information with Pangea: https://github.com/netcraftsmen/pangea/blob/main/playbooks/pb.breach_user_check.yml
Conclusion
Suppose you want to add selected security checking capability in your code without having to build and maintain databases of exposed or compromised information, malware sites and domains, etc. In that case, you should take a look at Pangea!
Let’s start a conversation! Contact us to see how NetCraftsmen experts can help with your complex challenges.