Much of the job of running a business is managing risk. Risk has many forms:
- Risk of competitors
- Risk of changing business environment
- Risk of supplier problems
- Risk of IT system failure
The last item is of particular concern since most business is now dependent on IT for much of its operation. Unfortunately, the risk of malware, particularly ransomware, has become significant in the last few years.
How Ransomware Works
Like most malware, ransomware works by infecting as many systems as it can. It uses various methods to gain an initial foothold, and then it spreads between systems within the organization. Firewalls are often not very effective. A common infection is via so-called spear-phishing attacks where an email is crafted to look like it comes from a trusted source. The recipient clicks on a link or opens an attachment that infects the recipient’s computer. Horizontal spread to adjacent computers can use brute-force password cracking, as was used in the Atlanta City government incident. Some malware, like WannaCry, spreads by taking advantage of unpatched vulnerabilities in operating systems.
Ransomware will typically use a few days to try to maximize its horizontal spread. It doesn’t wait too long because its signature may be identified, allowing it to be removed before it accomplishes its task.
When it is triggered, ransomware encrypts any files it can find and displays a ransomware message that demands payment via an anonymous mechanism, typically BitCoin, to a digital wallet. The wallet is changed regularly to avoid tracking. Payment must be made within a few days. The bad actors are incentivized to provide the encryption key when payment is made so that victims learn that paying is the quick path to resume business. Payment is typically one BitCoin per server, which can get quite expensive for widespread infection.
Minimizing Ransomware Risk
The bad actors are making a lot of money with ransomware. It’s not going to go away anytime soon, so we have to handle it. There are ways to minimize risk.
You probably have an IT security team. Does it include an incident response team and an incident response plan? Think ahead about how you want to handle a widespread ransomware infection. You should have already thought about what might trigger making the ransomware payment. The plan should include steps from initial detection through the restoration of service. Don’t forget to include the step of finding and remediating the vulnerability that allowed the intrusion so that you don’t get attacked again from that same avenue.
What steps can be taken to reduce the risk? First, implement the NSA foundational steps:
- Multi-Factor Authentication – Authentication based on what you know and what you have.
- Role-Based Access – Access to systems based on your role within the organization.
- Application Whitelisting – Permit systems to communicate only with those systems that are necessary for its function.
At NetCraftsmen, we recommend three additional steps that build a comprehensive foundation:
- Patching – A process of applying security patches to all IT systems in a timely manner.
- Network Segmentation – Compartmentalization of the IT systems to prevent the horizontal spread of malware that manages to make it in.
- Backups – Regularly backup all systems in a way that prevents malware from accessing the backups.
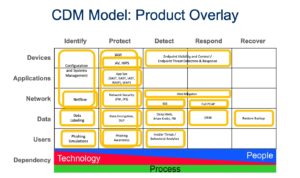
Upon this foundation, we recommend examining the IT security toolset from the perspective of the Cyber Defense Matrix (CDM), using a product overlay. It is easy to identify holes in the IT security systems using this matrix and product overlay. The bottom row identifies the mix of People, Process, and Technology (i.e., tools) that are required for each function across the matrix.
Measuring Your IT Security
You can use the foundation and the CDM to measure your organization’s IT security profile. In addition, NetCraftsmen can provide a security assessment. We use the above items with our people, processes, and technologies to provide a comprehensive security assessment. It is a great way to perform an impartial review of your systems and to identify technology holes, review people skills, examine processes, and strengthen your IT systems. The result is a lower risk to your business.