As you’d expect, Cisco did a great job of presenting at #NFD16. I’d have to say they dazzled us, with some solar contribution. In this post, I’ll summarize Cisco’s presentation, but for details, you’ll want to watch the video recordings.
Cisco split its time across two topics:
- Cisco Tetration
- Project Starship (pre-launch), now announced as Cisco Intersight
(Love the pun, since the latter product is also inter-site. One might even say the goal of the product is the ex-site-ing of UCS management.)
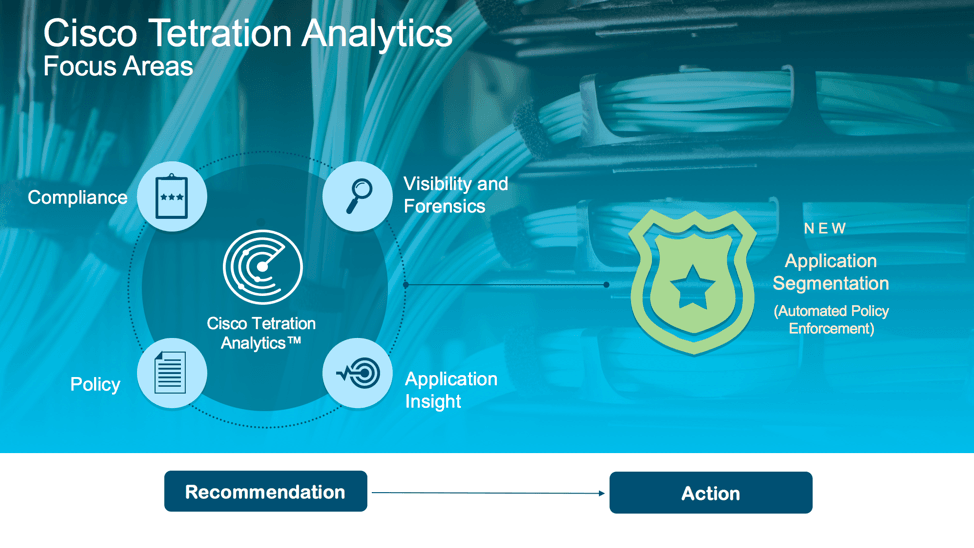
Tetration
My first impression: Tetration is clearly evolving and improving. It may be just me, but I think I heard more emphasis on agents and third-party sources, and less on Nexus 9K hardware. That makes sense in terms of not holding up purchase until hardware refresh time — something that previously may have deferred some/many ACI and Tetration buying decisions. Admittedly, hardware-based approaches have fewer touch points.
Initial customer interest in Tetration was light due to high price until recently, when smaller models became available.
The key point to me with anything like this or NetFlow, particularly for security applications, is that you really need to have ubiquitous coverage. Tetration does appear to potentially solve a lot of the problems with partial NetFlow deployments, or with performing a Network Packet Broker deployment. The Cisco presentation also certainly makes it appear the product is getting a lot of attention within Cisco and is rapidly maturing.
If you’ve read my prior blog posts, you know I’m a fan of using flows to understand applications better, especially before moving components to cloud or remote datacenters. That was the initial push with Tetration, in part since you need that info to migrate to ACI-based security.
More recently, and notably in the NFD16 presentation, Tetration is now also rapidly becoming more of a security alerting and mitigation tool.
Complementing all that, Tetration now has:
- ERSPAN input as an option
- NetFlow as an option
- Campus ISE integration, for ID awareness and context, and for policy enforcement
- Open API for Tetration Analytics: feed alerts to Kafka and notification event consumers, also for add-on apps
- Multi-tenancy, AAA, and RBAC
The presenters went on to talk about feeding Splunk and Phantom (see also my NFD16 Gigamon blog post), and Service Now. Yes, Cisco also talked about “Ecosystem”, as one would expect.
Hey, this was an X (X = Tech, Network) Field Day event, so of course there were demos and more! (Hint: see the videos.)
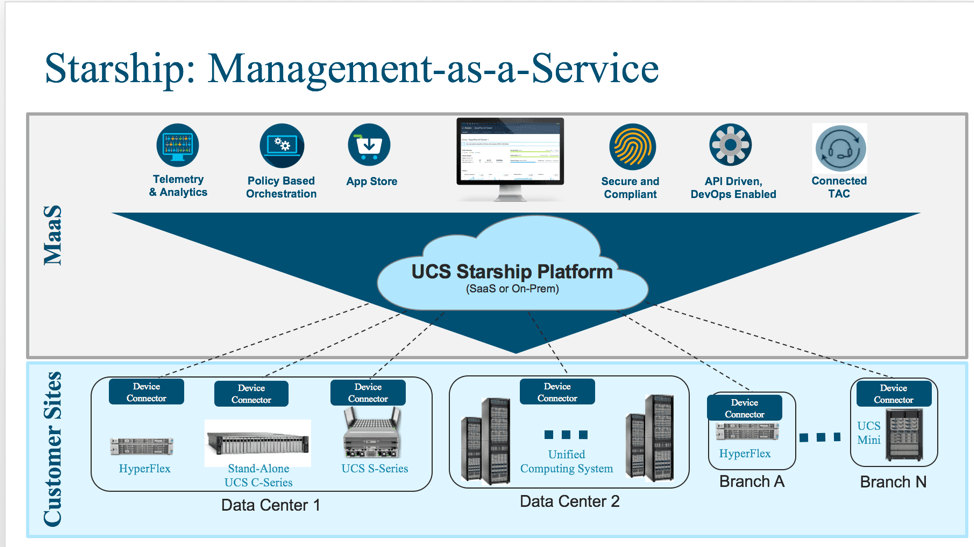
Project Starship (Now Launched as Cisco Intersight)
We got a pre-announcement view of Cisco Intersight. By the time these words appear, it will be well past launch date for that.
Concerning Intersight, I heard someone comment “Meraki-ize” UCSM, and that might not be far off base. Strength AND weakness: CI/CD (can you say: “instant bugs and quick fixes”?). There are some potentially compelling aspects for customers in the future (not initially):
- Fewer hassles around upgrading the management software
- Ability to bring domain knowledge and TAC experience to the customer’s installed base in an automated fashion
- Ability to potentially lower the amount of in-house or consultant expertise needed (consultant’s reaction: “darn!” <tongue in cheek>)
Think about it: With customer UCS systems feeding data to Cisco in an automated and ongoing way, Cisco will get great crowd-sourced data on failing components, common problems, etc. — particularly if they can correlate your gear with your TAC calls.
Other early impressions:
- The initial release seems kind of read-only, a Good Thing when building trust with a large customer base
- Functionality will grow, as (hopefully) will trust
- One hopes the registration and connection process will not be labor-intense or balky or slow
There is one aspect of Intersight that I really appreciate Cisco presenting on. There was a very strong effort that apparently went into securing the product. Cisco clearly does not want to become a vector by which their customers get hacked, via the tunnels from the SaaS offering back to the site UCSM. It sounds like security got baked into Intersight (and the coding and management teams) from day one.
See the videos for details. I imagine as the offering matures the slide decks will get more polished and detailed, but what’s in the videos gets things off to a great start!
References
My fellow NFD16 delegates and Cisco have been busily blogging boldly, per below:
- NFD16 day two – Cisco Project Starship a.k.a. Intersight
- Is the Data-Driven Network Next Step in Networking?
- Cisco Intersight – A Transformative Evolution
- Cisco Launches Intersight: Cloud Managed UCS and HyperFlex
- Seeing Tetration in action – NFD16
Comments
Comments are welcome, both in agreement or constructive disagreement about the above. I enjoy hearing from readers and carrying on deeper discussion via comments. Thanks in advance!