This is the 14th blog in an Internet Edge series.
Links to prior blogs in the series:
- Internet Edge:Simple Sites
- Internet Edge:Fitting in SD-WAN
- Internet Edge:Things to Not Do (Part 1)
- Internet Edge: Things to Not Do (Part 2)
- Internet Edge: Two Data Centers
- Internet Edge: Double Don’t Do This
- Internet Edge: Cloudy Internet Edge
- Internet Edge: Special Cases and Maintainability
- Internet Edge: Security Tool Insertion
- Internet Edge: Internet Edge: Traffic Steering Part 1
- Internet Edge: Internet Edge: Traffic Steering Part 2
- Internet Edge: Internet Edge: Traffic Steering Part 3
- Internet Edge: The Big Picture
- Internet Edge: Application Resiliency
We’ve reached the point of having pretty much exhausted the “Internet Edge” theme. It is amusing to note in a just-published blog, Cisco says there is no enterprise perimeter to defend anymore, and we all probably agree with that. Apparently, I got this series written just in time!
I’ve drafted a blog discussing how software on endpoints, and perhaps smart NICs in servers, may change the game. Does more functionality move off network devices, distributed across endpoints? I plan to cover that in the later blog since it falls somewhat outside the “Internet Edge” scope of this series. We’ll get into endpoint-based security a bit in this blog as well.
Aside from the data center, there are other variants of edge security, namely endpoint-based and cloud-based. The two categories overlap when most of the endpoint-based security functionality is actually in the cloud.
Cisco, zScaler, and likely other companies are selling solutions in this space, cloud-based security services.
Why?
But first, why would you want to use cloud-based security services? And wouldn’t they be slow due to high latency, since your site or endpoint to Internet traffic would be going out through a cloud presence somewhere?
The biggest reasons are staffing and costs. Security has gotten complex, and keeping up is a full-time job in itself across multiple aspects of security.
Small to medium-sized, perhaps even fairly large companies may find it hard to hire enough skilled people and do a good job of security overall. They may do better by offloading what they can to an outside organization to focus internal staff on what needs to be done in-house.
The second answer is WFH (Work From Home) – aka mobile users. The future may well have staff working from home 2-3 days/week, or full-time. Staff may not always be at a site with a router / SD-WAN router, firewall, etc. Yet you need to secure their laptop or whatever device they are using for work.
How These Products Work
zScaler perhaps pioneered the idea of an Internet-based firewall service for sites. You would either configure your Internet router to tunnel traffic to zScaler, or configure endpoint web proxying at the site to do that for you. They would then provide security services. Over time, the security services provided via the cloud expanded. And standalone endpoint functionality was added.
Cisco acquired Umbrella a few years back. You would point your site DNS at it. It then acted as a DNS resolver that would block access to untrusted/low reputation sites, etc. Another aspect was a large worldwide presence at key Internet locations, providing low-latency connectivity to nearby users/sites.
Since then, Cisco has increased the Umbrella security functionality while also coming out with an endpoint-centric version of its products. The end system version is now sold as “Secure Internet Gateway (SIG).” It proxies user traffic tunneled to it in various ways.
In the Cisco networking space, the Cisco Viptela SD-WAN products and now Meraki firewalls have simple integration with the Umbrella offering.
Concerning endpoints or SD-WAN routers, the key thing about these products is that all the security-related tasks don’t have to be actually located on the endpoint or router. With anycast or other distributed services in many global points of presence near most users, cloud-based services can provide a very viable alternative without severe latency penalties.
Other advantages: possibly smaller endpoint footprint, easier / faster updates by the provider, low support costs. And the ability for a small to medium-sized organization to offload security to a major service provider, rather than struggling to adequately staff it in-house.
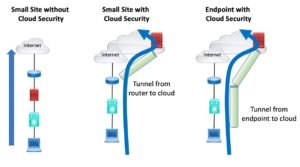
The following diagram attempts to show what is different about cloud-based security. A firewall icon superimposed on the cloud is used to indicate the cloud-based traffic processing that is being done.
What The Cloud Security Products Do
The network device products augment the access list / firewalling functionality in the router or SD-WAN router.
For endpoints, Umbrella Secure Internet Gateway now includes the following:
- DNS security
- Secure web gateway
- Cloud firewall
- IPS functionality based on Snort 3
- Malware detection and removal with reporting and cloud storage scanning
- CASB (Cloud Access Security Broker)
- Interactive threat intelligence
- Fast query by admins to speed up and simplify threat hunting
zScaler Client Connector HTTP tunnels traffic to their cloud platform, where corporate policy is applied. Tunneling is turned off when on a trusted network. The zScaler web pages are a bit vague about the specific functions it provides, but it appears secure web gateway, cloud firewall, URL filtering, and malicious behavior detection are included.
Cisco also has a cloud-based version of its AMP code now, AMP Secure Endpoint.
AMP Secure Endpoint provides:
- Antivirus protection
- Behavioral monitoring
- Dynamic file analysis
- Advanced endpoint detection and response, Threat Grid Cloud
- Threat hunting
- Endpoint isolation
- Database and search with endpoint information
So you can get AMPed via that on your endpoint, or via firewall-based AMP, virtual AMP for cloud, or Meraki and Cisco Viptela SD-WAN functionality. I suspect the Meraki tunnels to the cloud version. Training materials for the Cisco Viptela SD-WAN indicated that (at that time anyway) Cisco was running AMP code in a container on the SD-WAN router for fastest processing and punting to the cloud when necessary.
Links
- zScaler
- zScaler Client Connector
- Cisco Umbrella / Secure Internet Gateway
- Cisco Umbrella
- Cisco AMP for Endpoints (Secure Endpoint)
- Cisco AMP
- 5/19/21 Network World article
Conclusion
The classic Internet Edge is not going away. We still have onsite users and data center servers that need to be protected. But we also now have to protect mobile users and remote sites. If we can deploy an SD-WAN router to small sites and NOT have to deploy a firewall, that’s a cost and deployment/maintenance saving. Central cloud management of security versus managing security across a fleet of small routers, ditto.
And concerning users, securing their workstation without having to deploy a remote AP or router or a small SD-WAN router to their home has the additional benefit of providing protection when they are mobile, not at home nor in the office.
Food for thought: if your users are covered by the cloud solution, even when in the office, does that change how you structure office protection? If so, how? One thought is that perhaps the “user firewall” between users and the data center (and perhaps the Internet) does not have to do as much work. What do you think?